The present-day network might seem smooth sailing on the surface, yet the backdrop of all such successful connections involves a well-planned system in place. Information should be transferred between an application on the device in one location, and then it has to traverse several networks and get to the destination location intact. The reason why the Open Systems Interconnection (OSI) Model exists is to describe the manner in which this complicated procedure occurs in a structured and standardized manner.
The OSI model is a theoretical model that divides the communication in networks into seven levels. Instead of being concerned with the protocols or technologies, it outlines what must occur at every level of communication. This multifaceted strategy gives various systems, vendors, and technologies a chance to communicate with each other more attentively by following an identical reference model. Although the OSI model is not a protocol, it is very important in the way engineers design, analyse, and secure modern networks.
The Importance for Network Security
The capability of simplifying complexity is one of the most useful items of the OSI model. Networking is a complex machine with lots of moving components, and without an organized method of defining the components, troubleshooting and security investigation would become much harder. The OSI model allows professionals to isolate the issues, learn the attack surfaces, and assess security controls more accurately because it divides responsibilities into layers.
This abstraction is particularly strong, as far as security is concerned. The network is not affected by cyber threats equally across, but rather, these threats target the layers. There are attacks that take advantage of physical infrastructure vulnerabilities, attacks that target routing logic and transport mechanisms, and attacks that target application vulnerabilities. Satirically, with the OSI model, security teams can easily understand the location of an attack and which controls are best at countering an attack.
Even though modern networking does not need the OSI Model to operate, the model is still necessary in education, planning, and security strategy. It offers a common language to be used in the planning of risks, defences, and architecture across teams and organizations.
7 Layers of OSI Model
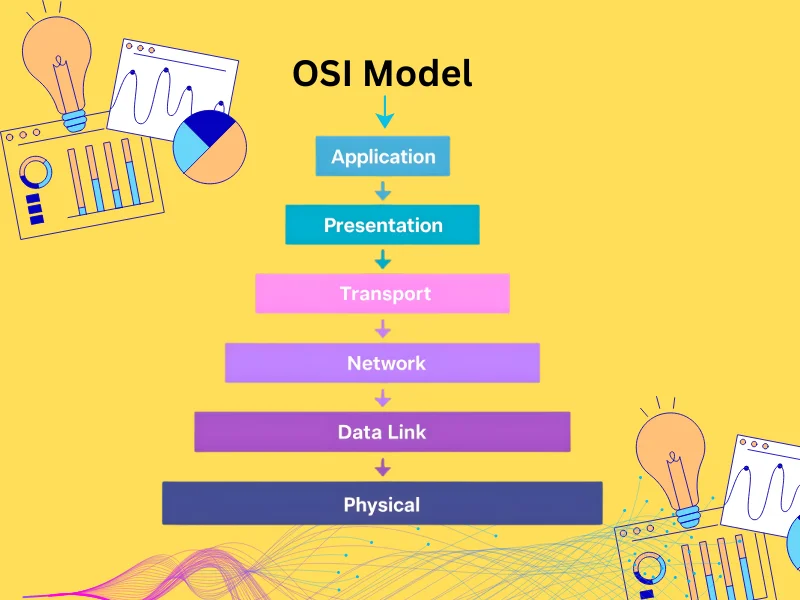
The OSI model is made up of seven layers, with each having a distinct role in the communication process. The layers collaborate with each other by sharing protocol data units (PDUs) and make data flow efficiently between the sender and the receiver.
Each layer is usually denoted by both name and number, with the lowest level (which is Layer 1) and the highest level (which is Layer 7). The different layers are built on top of each other with a new functionality and context.
#1. The Physical Layer
The physical layer is the base of network communication. It is the one that makes the raw bits be delivered by some physical medium consisting of copper cables, fiber optics, or even wireless waves. Here, the data is encoded as electrical impulses, light pulses, or radio waves.
The symbol is referred to as the Layer 1 PDU. This layer specifies physical traits such as voltage, signal timing, data rates, connectors, and transmission modes. The physical layer is the most basic and thus the least recognized component of the network stack, as without it, there can be no data transferred between devices.
#2. The Data Link Layer
The data link layer provides the dependability of communication between two devices that are in direct contact. It receives the stream of bits in the physical layer in its raw form and encodes them into frames.
Tasks that are dealt with by this layer include error detection, flow control, and media access control. It also controls the way devices name each other via hardware addresses and the time when or end a connection. The Data Link Layer will ensure that any corrupted information does not proceed any higher along the stack by correcting any errors that occur.
#3. The Network Layer
The Data Link Layer deals with a direct connection, whereas the Network Layer deals with communication between various interconnected networks. Its main duty is to send packets between the source and the destination through logical addresses, e.g., IP addresses.
Network-layer devices such as routers examine packets and identify the most efficient route across the network. This layer is important in terms of scalability, where data can pass through complicated global networks as opposed to being limited to a local segment.
#4. The Transport Layer
The host layer is the first of the four communication layers known as the Transport Layer, as it is concerned with end-to-end communication and not the transmission medium. Information on this level is summarized into segments or datagrams.
This layer guarantees the stable delivery of data through controlling sequencing, acknowledgments, and error recovery. It dictates the level of accuracy or speed of communication. Transmission Control Protocol (TCP), which delivers information reliably and in order, is used at this layer, and so is the faster but less reliable User Datagram Protocol (UDP).
#5. The Session Layer
The session layer handles active communication between devices. It takes care of creating, sustaining, and dissolving sessions, and the data exchanges are required to be organized and controlled.
This layer provides authentication and session recovery, besides the configuration and de-configuration of a session. In case of a disabled connection, the session layer may be used to restart the communication without having to restart the entire data transfer.
#6. The Presentation Layer
The presentation layer works as an interpreter between the network and the application. Its main purpose is to make sure that the information sent by one system may be properly interpreted by a different one, despite any differences in the format or coding.
Such tasks, such as data compression, character encoding, and encryption, are performed in this layer. The presentation layer helps to ensure safe and uniform communication between different systems because of the standardization of data representation.
#7. The Application Layer
The Application Layer is where users directly interact with network services. It includes protocols designed to support specific applications and use cases.
Examples include HTTP for web browsing, SMTP for email transmission, and FTP for file transfers. This layer does not represent applications themselves, but rather the protocols that applications use to communicate over the network.
Network Layers: OSI vs TCP/IP
The OSIS model is not the only model that is applied to explain networking. Another model, the TCP/IP model, predates OSI and is more widely used and fits better into the real-world implementation of protocols.
TCP/IP is a model with four layers:
Application Layer: This layer is a combination of the Application, Presentation, and Session layers of the OSI Model. Here, protocols like HTTP, SMTP, P, and DNS are used.
Transport Layer: This level is equivalent to the OSI Transport Layer, and it needs to contain TCP and UDP.
Internet Layer: This layer is directly analogous to the OSI Network Layer and is, to a great extent, controlled by the Internet Protocol (IP) and the protocols it relies on, such as ICMP and ARP.
Network Access Layer: This layer combines the Physical and Data Link layers of the OSI Model and encompasses technologies like Ethernet, Frame Relay, and more.
Although the OSI model is a more detailed and theoretical representation, the TCP/IP model reflects the real construction and implementation of networks. They are complementary to each other in terms of network architecture.
Advantages of the OSI Model
The clarity of the OSI model is one of its most significant strengths. Defining the responsibilities by each level will assist the professionals in seeing the path travelled by the data across a network and where problems can occur.
This organized method makes the process of troubleshooting much easier and also facilitates the secure design of networks and eases the process of analysing attacks and vulnerabilities. It also promotes interoperability since it promotes standardized communication techniques between vendors and technologies.
Solutions and the OSI Model
The different layers of the OSI may be the target of cyberattacks according to the goals. An example of these attacks is Distributed Denial of Service (DDoS), which can seek to saturate network bandwidth at Layers 3 and 4 or inundate applications at Layer 7.
An effective enterprise security plan should offer visibility and security to all the host layers, especially the 4th to 7th, where most of the modern attacks are witnessed. Solutions such as Quantum Network Security are created to monitor traffic at these layers and help organizations to identify threats, implement policies, and take effective actions.